In the last 30 days, we did massive posts, all centered around Privacy and Anonymity, and this is supposed to be the final, longest, and most detailed post in the same series, probably the best(est) guide on A-Z aspects of Privacy tools on the web.
By the end of this guide, there won’t be an inch of crack left in your security wall that can be breached to infiltrate your privacy and anonymity.
51 Best Privacy Tools
Just so you know what to expect of this guide, and so that I justify what I’ve just claimed, I’ll be sharing detailed guides, along with a number of tools for each of the following-
- Anonymous and Private Operating Systems
- Network Security.
- Browser Based Security.
- Password Security
- Search Engine Privacy
- Hard Disk Security
- Anonymous and Encrypted E-mails
- Communication Security
- File-sharing security.
I believe that should cover nearly every digital footprint or existence most of us have in our lives, don’t you agree?
So without further adieu, let’s get started.
Anonymous Operating Systems
Anonymous operating systems are the kind of operating systems which in one way or other empower you with a Fort-Knox like security and anonymity.
Meaning, it’s next to impossible to hack into these systems, or infect them with a Virus, Malware, Trojan or anything else.
Which is exactly opposite of what most mainstream operating systems like Windows and Mac are vulnerable to.
And it’s not just about viruses and infiltration, these Anonymous operating systems are designed to provide you the features and latitude which let you browse anonymously, protect your privacy online as well as offline, and in some cases even get you offensive security measures (such as with Kali Linux).
These operating systems do not send any information related to your activities, location or anything else to any website, third-party, or even the creators of the operating systems.
Some of the common features to most of these privacy tools are their ability to route every outgoing connection via the Tor network, and their pre-installed bundles of a number of security and anonymity promoting tools for messaging, E-mail and everything else.
These operating systems also include advanced encryption algorithms for your HDDs, as well as external storage devices and drives such as USBs and CDs.
And just in case you’re wondering, yeah these are the perfect operating systems for you in case you wish to browse the Deep web without leaving footprints for agencies and hackers to find.
Now that you’ve got a decent idea of what these operating systems are made for, let me share some of these with you.
1. TAILS
Website: https://tails.boum.org/
TAILS stands for The Amnesic Incognito Live System. It’s literally the best privacy tool out there, especially when it comes to an operating system which is anonymous, and not only respects your privacy, but “encourages” it.
It can be used directly from a USB stick or a CD, without formal “installation”, and hence leaves no trace on the system it’s used on.
It’s a project partially funded by Tor itself, so obviously it promotes uncensored internet and hence all and any traffic from the system is routed via Tor.
In fact a number of security tools which we will discuss in this Privacy tools guide are pre-included with TAILS, such as HTTPS Everywhere, Pidgin and Thunderbird etc to make it as digitally secure as possible.
It also includes quite a few advanced encryption protocols for encrypting every inch of your system, activities and storage devices.
Bottomline, in case you need an anonymous and private environment complete with uncensored E-mail clients, messaging platforms, browsers and everything else TAILS is the answer.
2. Whonix
Website: https://www.whonix.org/
Whonix is another one of the best Privacy tools and anonymous operating systems that deserves our attention.
It’s a project based on Tor, and all traffic like TAILS is routed via Tor. In addition to that, it boasts a custom tailored Debian base which is run inside multiple virtual machines to make IP leaks or malware attacks impossible.
It’s a LIVE OS, so it can be run directly from a USB or CD disk and no trace is left on the system again alike Tails.
As far as tools go, it has stocked its arsenal up with a number of decentralized and anonymous tools for E-mail, messaging, in addition to pre-installed Tor and hidden IRC servers.
So yes, as an operating system it’s pretty good at keeping your identity and activities off the grid, exactly what we’re looking for isn’t it?
3. Qubes
Website: https://www.qubes-os.org/
Qubes is one of the most trusted anonymous OS on the planet, which has been vouched for by “The Edward Snowden” himself.
It has this exclusive and unique feature of “compartmentalization” of each individual app and program run on your system hence creating an impregnable wall between each of them.
Meaning, each app you run is run as if it’s on a “different” system, so in case any one of them is compromised, neither the whole system, nor any other app will be compromised hence making it one of the most secure privacy tools and best privacy software out there.
Additionally, what makes Qubes special is that it can be used to run not only “Windows apps”, but those of Linux, Fedora or even Whonix.
I believe we’ve talked quite a bit about operating systems, although you can get more options from this detailed list on 7 best anonymous OS for Tor.
Let’s move on to the next aspect of this Privacy tools guide- Online privacy tools; which will keep you “Internet activities” anonymous.
Network Security
Network security is here used to denote “Internet connection security”, meaning ways, methods and privacy tools which will help you keep your “Internet connection” secure and anonymous.
In case you’re totally new to this, let me just get the basics straight. When you connect your offline computer to the Internet, it’s done so via your ISP (Internet service provider).
Now the ISP has quite a bit of control over your connection, they can trace your location, activities, block certain websites if they wish to, and things like that.
Even if the ISP doesn’t do anything, the general, unsecure internet connection isn’t secure enough, and any kid with 5 minutes on Youtube can learn how to intercept your traffic, hack into it, install a backdoor on your system, or get access to your physical location in the least.
More advanced threats include hackers being able to modify your search history, force redirects you to certain websites, or even hack into your Webcam in some cases.
Bottomline? Plain, unsecure internet isn’t how the internet should be accessed. Now that’s what we will solve in this section.
In order to protect your internet connection from third-parties, and even from your ISP, you need a VPN, and optionally a router.
A VPN is an abbreviation for “Virtual Private Network”, in the simplest possible words I can explain a VPN as being one of the best, simplest privacy protection software in existence.
What a VPN does is, it primarily encrypts your internet traffic and changes your IP address. Now this IP address is what connects your computer, to the internet. When you change your IP address, neither your ISP nor anyone else gets to know your new IP address.
These new, masked IP addresses assigned to you can’t be traced back to you in any way (if the VPN is good enough), and hence you appear to be from a different country (which you get to choose).
And because the IP addresses lead to a “server” (of the VPN company, and not your actual computer), and because the connection is encrypted, it can’t be used to hack into your system, trace or track your activities or block any websites either.
So here are the best privacy VPN and the router I personally trust and use to get myself the best online security that there is.
1. NordVPN
Website: https://nordvpn.com
NordVPN is my most trusted VPN, and it has been so for at least 4 years now, not without reasons though.
The primary reason why it gets my high vote of confidence is because of its “No logs policy”, meaning it doesn’t “log” your IP address, or any other activities!
That’s what makes it one of the best anonymity tools because not a lot of VPNs truly offer this feature!
Sure, every VPN claims of not logging activities and addresses, most of those claims are fake. Unlike them, NordVPN got its “no log policy” publicly and independently audited. That’s what makes it literally the best VPN out there. It can’t sell you out even if it wanted to.
Moreover, it’s not based in the US/EU and rather is headquartered in Panama. Meaning, the chances of more stricter governments holding any control over it are slim anyway.
Also, we could list any VPN here. But, none have provided us with the speed that NordVPN does. Your privacy shouldn’t cost you speed, should it? NordVPN is literally the fastest VPN out there. It supports NordLynx which makes these unprecedented speeds possible.
Also, I’m sure most of you download torrents and/or share files over P2P. It’s one of the only VPNs which not only allows, but also encourages you to do so. Do you know torrenting without a VPN means your IP address is literally “published” on the web? NordVPN prevents that.
Its vast availability of countries and servers, along with its unbreakable encryption algorithms are equally impressive.
It gets us a list of 60+ countries to choose from, and has a total of 5500+ servers, which is a big deal in today’s VPN industry.
Its servers are further categorized into a number of different categories based on their purposes and specialty, such as Anti-DDoS, Double VPN, Onion over VPN, Dedicated IP servers etc.
And when it comes to encryption, it supports the 4 most secure connection protocols available, namely – OpenVPN, L2TP/ IPSec, PPTP and IKeV2.
You can read a complete, detailed NordVPN Review here, but for now let’s just say it’s one of the best VPNs you can employ to save yourself from the censorship wrath out there.
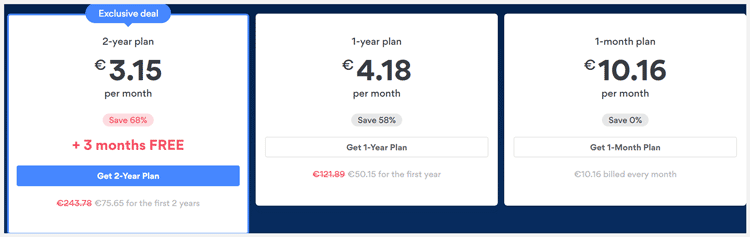
- NordVPN Simple Plan $10.16/Month (Monthly Subscription)
- NordVPN Standard Plan $4.18/Month (Yearly Subscription)
- NordVPN Best Offer $3.15/Month (2 Year Subscription)
- NordVPN Cyber Sale $3.15/Month (2 Year Subscription)
2. IpVanish
Website: https://ipvanish.com
 IPVanish is the second VPN you could get in case you aren’t going with NordVPN. The features are more or less the same so you won’t be missing anything significant with this one either and it still is one of the best privacy tools.
IPVanish is the second VPN you could get in case you aren’t going with NordVPN. The features are more or less the same so you won’t be missing anything significant with this one either and it still is one of the best privacy tools.
It too offers us 60+ countries to choose from, although when it comes to servers it only has around 900 functional servers (not that it makes a big difference for us as users).
As far as IP addresses go, it has a massive 40,000+ shared IP address database! It employs 256-bit military grade encryptions to encrypt its connections, along with 3 other connection protocols (OpenVPN / PPTP / L2TP/IPSec).
It too has a “Zero logs policy” in place hence no activity logs are kept, and supports as many as 5 devices to be used simultaneously for the same account as well.
So bottom line, it totally is one of the best privacy tools and pretty light on the pocket as well. You can read a complete IPVanish VPN Review here.
- IPVanish $10.00/Month (Monthly Subscription)
- IPVanish $8.99/Month (3 Month Subscription)
- IPVanish Best Value $6.49/Month (1 Year Subscription)
3. ExpressVPN
Website: https://www.expressvpn.com/
ExpressVPN is the second most sought-after VPN after NordVPN; infact it supports as many as 94 countries to choose from, while Nord does only 61; however the number of servers which determine the performance of the VPN connection on Nord are nearly double; i.e. 5400 as compared to the 3000 servers with ExpressVPN.
As for security, there’s the traditional 256-bit military grade encryption; followed by a Kill-switch (auto-disconnects the system from internet if the VPN drops); DNS/IPv6 Leak Protection (Makes sure the system always uses the VPN to connect to the Internet) and even Split Tunneling.
Has a no logs policy which also extends to connections, meaning neither user-profile data; nor data related to their connection (IP addresses, web activity) etc. are kept. After NordVPN, it’s the only company which has been publicly and independently audited to not store any logs. The only reason why I’ve kept it lower than NordVPN is because it’s comparatively slower, unblocks fewer Netflix libraries and is a lot more expensive than NordVPN.
Support Protocols including OpenVPN, SSTP, L2TP/IPSec, and PPTP. Also provides a 30-day moneyback guarantee.
- ExpressVPN $12.95/Month (Monthly Subscription)
- ExpressVPN $9.99/Month (6 Month Subscription)
- ExpressVPN Best Value $8.32/Month (1 Year Subscription)
3. Asus RT-AC5300 Router
Website: https://www.flashrouters.com/
We’ve talked of VPNs, as a final nail to the coffin of network breaches, let’s briefly discuss routers as well.
The Asus RT-AC5300 is just another internet router, but with the capability of letting you install and use a VPN on it.
Because the VPN is installed on the router, the VPN connection protects all the devices connected to the router in your office, or home.
Apart from the VPN support, it boasts quite a few core-features of its own such as Link aggression which allows you to double your wired internet speed by joining two LAN cables.
In addition to its support for 802.11ac standards along with Beamforming giving the router magical powers to auto-locate exactly where your devices are and serve you better speed and stability.
It supports MU-MIMO technology as well, and finally as it’s a flash router, it’s pre-flashed with DD-WRT, probably the best custom firmware out there for a lot more security, stability and features than the naked router.
So in a nutshell, if you connect a lot of devices to the internet, the router is a nice addition to your VPN for a completely secure network!
Read the complete Asus RT- AC5300 review here.
- Best VPN Router for Small Business
- Best DD-WRT Router List for Home or Small Office
- Best VPN Router for Home
- 4 Best Router for Tomato Firmware
Browser Based Security
We’ve covered a secure operating system, and network security by now. But aren’t we missing a core component of today’s computer systems?
Web browsers! Yes! Those are what we use to actually connect to the internet, and browse websites, so naturally they too can be compromised and hacked into.
Browser security basically includes privacy tools which make sure your activities on the web, your history, cache, location information, browsing habits or saved passwords aren’t leaked out to third parties.
These security measures are either implemented by the browsers themselves, or at times, by third party add-ons and extensions, all of which we will cover in this section.
Tor Browser
Website: https://www.torproject.org/
Tor is the most famed name that pops up in any discussion even remotely related to the best internet privacy software, doesn’t it?
Tor stands for The Onion Router, and it routes all its traffic via the Onion network. The Onion network is the part of the web, which is uncensored, and independent, unlike the clearnet where every single site and its users are subject to a thousand laws and regulations.
It routes all your traffic via a number of “relays” which are next to impossible to connect to each other hence making it hard to trace you on the web.
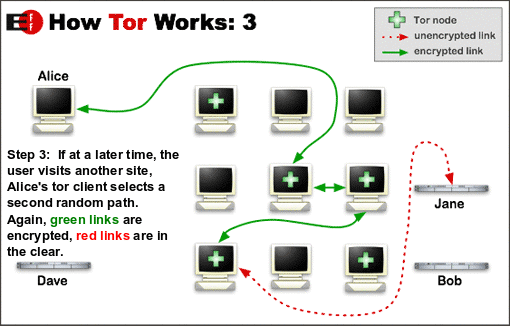
In a nutshell Tor browser doesn’t let anyone spy on your activities, location, or any other information related to you. Neither does it collect any such information itself. It disables javascript and doesn’t log your cache or cookies either.
It’s a free, open-source project run by volunteers, lets you browse .onion (deep web) links, and is the perfect solution for you if you wish to keep your identity private and anonymous, or go stroll around the deep web.
EPIC Browser
Website: https://www.epicbrowser.com
The Epic browser is the second name that should be your guardian angel on the web in case for some reasons you aren’t going with Tor.
One of its unique features making it one of the best privacy tools is its “isolation”, meaning every single outgoing connection is an independent process, so breaching any one single connection won’t lead to your whole connection being breached.
In addition to that, it has this capability of blocking every single element on a website which can be used to trace and track you, your activities, or your preferences. These elements include HTML 5 Storage, cookies, ever cookies, flash cookies etc.
There’s also an inbuilt proxy to help you mask your IP address in case you aren’t using a VPN from your end manually, although you can use EPIC’s proxy with an additional VPN of your own as well.
It even protects us against fingerprinting and image canvas. It doesn’t log our history, passwords, spell-checks, DNS cache, Web-cache or anything else which can in any fickle way lead to our privacy being compromised.
It doesn’t even send “Referrer head data” to websites when you hop from a search engine link to a site.
Finally, EPIC has this awesome feature which lets you spy on your spies by showing you who or which sites exactly are tracking you.
Website: https://brave.com
Brave is a join project by the Founder of Javascript and Mozilla Co-founder! That already speaks volumes for the brains behind the project.
The browser auto-detects malwares and other security threats and prevents them from harming users. It even disables harmful plugins by default. As for personal data; it’s neither accessible nor stored by the browser (which Chrome and most other traditional browsers shamelessly do).
It also is capable of Fingerprint blocking which prevents sites from tracking and identifying users and their activities on the Internet; obviously there’s the ad blocker as well.
It lets users customize the browser on two fronts- For individual sites; as well as for all sites in general. It also has the “Do not track” browsing request feature. An exclusive feature is that it understands that web content creators may be losing money with their ads blocked, hence it lets users donate money to sites using Cryptocurrencies.
They also claim double browsing speed than Desktop; and as much as 8x faster speeds on Mobile than Chrome. Also you won’t be losing much of Google chrome’s functionalities or add-ons either as the Desktop version of Brave supports almost all Chrome extensions from the Chrome store.
Adblock Plus
Website: https://chrome.google.com/
AdBlock plus is obviously one of the best privacy tools, but isn’t exactly a browser, rather it’s an extension which can be embedded with Chrome, Mozilla, Internet Explorer, Safari or every other major as well as minor web browser out there.
As the name suggests, it primarily “blocks ads”. That means better browsing experience and less distractions.
It blocks not just “banners ads”, but Facebook Ads, popups, flashy ads, pop unders and everything else!
Although not all ads are blocked, and some “acceptable” ads are shown in order to support the websites showing them. In my personal opinion and experience, these acceptable ads actually are almost always acceptable and non-intrusive.
Although this feature can be disabled and you can have a 100% ad-free browsing experience should you wish so.
Adblock Plus doesn’t limit itself to just blocking ads, but also “trackers and malware” as well, so your anonymity and privacy remain safe, your data isn’t leaked, and neither is your system at risk from malware floating around the web.
The malware protection feature was enabled by default, but I recently found out that it can be extended to block “all” suspicious domains as well which is a nice addition.
And finally, it also has the capability to block social share buttons, which otherwise can lead to your browsing habits and preferences being shared with the social media and a number of other third-parties.
Privacy Badger
Website: https://www.eff.org/
Privacy Badger isn’t an “adblocker” rather a privacy tool is what they claim even though it’s based on Adblocker’s code; it does have its own differences.
The primary difference is that, while Adblock Plus needs the user to play around with its settings and customizations to achieve satisfactory results, Privacy Badger doesn’t!
It’s based on the model that it should be able to function and work for the user without any interference by the user, based on an advanced algorithm.
What it primarily does is, it follows you around on the web as any extension would do, and verifies the third-party elements which load up on the pages you visit, if any single or suspicious third-party seems to track you across various pages, it blocks the third-parties scripts from loading in the future.
Although it does make exceptions in case there are crucial codes to be loaded, such as for Maps or images, but even in those cases it’ll filter out the elements which can be used to track you.
The reason Privacy Badger has termed itself as one of the privacy tools and not an adblocker is because as they say, their prime endeavour isn’t to “block ads” but to block “intrusive, objectionable” ads.
It also “freezes” social media buttons so that they can’t “track your habits or pages”, which otherwise they do; unless you explicitly “click” on them.
Qwant
Website: https://www.qwant.com
Qwant is a privacy search engine made in France. This immediately offers it advantages which companies based out of US/UK or most other countries do not have in terms of data protection or anonymity.
It doesn’t use any code or devices which can track you around the web. This includes pixels and fingerprinting. None of that exists on Qwant. It also doesn’t put cookies on your browser which makes sure you can’t be recognized or put into a profile.
Obviously, no search history is stored either. Nothing which can be linked to your IP address or “you” in person is stored on Qwant servers or anywhere else.
It’s pretty feature-rich as well. for starters, It allows searching for images, videos, maps, music and a lot more. You can even filter results based on “location/country” in addition to date. Obviously there are absolutely no ads.
Just in case you use your phone more than a computer, Qwant features both anAndroid as well as an iOS app.
LibreWolf
Website: https://librewolf-community.gitlab.io/
Three words- Open source, free and privacy-oriented. Clearly it’s one of the best privacy tools you can find for browsing the internet.
It’s based off the Firefox open-source code so there are no hidden agendas here. That’s not me saying, it can be verified by anyone who speaks code.
Its even uses anonymous search engines by default such as Duck Duck Go, Qwant etc. uBlock Origin an ad-blocker is pre-included with the package.
Its most impressive feature is that it doesn’t use Telemetries. You won’t be fingerprinted and there’s no adware.
The only hiccup is you don’t get a setup.exe for download. You must compile it on your own using the source code.
Ghostery
Website: https://www.ghostery.com/
Ghostery again is a browser extension, which helps you browse faster and safer on the web. The one feature which distinctly is better in Ghostery than the other two options above is its user-interface and dashboard!
Its anti-blocking technology too is slightly different than the usual adblockers. It doesn’t just block all third-party elements, instead analyzes and verifies the requests being sent, and simply strips them off “identifiable” information.
It also functions on a “Filter list”, meaning automatically vets which ads are to be blocked and which to be allowed based on the list, totally without user-interference.
In addition to that, it also automatically calculates the threat or problem a tracker may cause you, hence blocking extremely slow or non-secure trackers, while in other cases allowing others.
And like EPIC it too has this feature which lets you spy on your spies, by showing you who is tracking you, and what information exactly is being collected.
And lastly, it’s free, and doesn’t require you to must-have an account in order to use Ghostery making it one of the best privacy tools or extensions out there.
Temporary Containers
Website: https://addons.mozilla.org/en-US/firefox/addon/temporary-containers/
As the name suggests, it creates “temporary containers” for your browser. In simpler words, it lets you create separate and independent tabs.
You can use these tabs for any and all activities. The benefit you get is that the cache, cookies or other data is burned as soon as you close the last tab.
It does allow for a few customizations, especially with its colours and icons. Do note that it doesn’t make you “anonymous” like the Tor browser does.
It simply stores your cache, cookies and other data in a separate, temporary container.
This does mean that you won’t be fingerprinted or “personalized ads” won’t invade your privacy.
Netalyzer
Website: http://netalyzr.icsi.berkeley.edu
Netalyzer isn’t a browser, or even a browser extension, rather it’s a more hardcore solution to solving your internet problems in the form of a web-based results tool.
In simple words, it “Analyzes your Internet connection” (Net + Analyzer) for privacy concerns, important requests being or not being blocked and things like that.
In most cases, for most general users it won’t make sense unless you’re well versed in error codes, ports and such stuff.
But if you are, it can prove to be one of the most detailed, useful and comprehensive result of all and everything related to your internet connection.
It includes HTTPS tests, DNS tests, IPV6 Tests, Network link properties and much more.
For every single issue, there are detailed explanations of what’s causing it, although note that there aren’t any “recommended solutions” so you’ll have to understand and fix the problem yourselves.
How about we lean towards a different section of this Privacy tools guide now, something simpler to understand? Password Security? Yeah let’s get it done!
Password Security
This section of this Privacy tools guide is dedicated towards password security because hey, passwords are your keys for various sites, aren’t they?
So obviously, remembering them, keeping them safe, and better organized is extremely important, isn’t it?
Unfortunately, typing all your passwords on a notepad file and saving it on your computer is the worst way to keep your passwords safe. Anyone with physical access can have a glance over them.
Even remotely, anyone can install a keylogger and compromise your security to the core, or a more advanced threat is someone extracting saved passwords off your browsers (yeah it’s possible).
Bottomline, you need a secret “vault” of sorts to keep your passwords safe and organized and that’s what the following tools provide.
Website: https://nordpass.com/
 NordPass is a product offered by the revered NordVPN team. It recently came up with this Zero-Knowledge, completely encrypted password manager. Zero-Knowledge as you know makes sure the company doesn’t have access to the stored passwords on the application. It has been independently audited by “Cure53” for its claims and they found all its claims true.
NordPass is a product offered by the revered NordVPN team. It recently came up with this Zero-Knowledge, completely encrypted password manager. Zero-Knowledge as you know makes sure the company doesn’t have access to the stored passwords on the application. It has been independently audited by “Cure53” for its claims and they found all its claims true.
A pretty recent and very strong encryption protocol- XChaCha20 is used to encrypt the passwords.
One of NordPass’ impressive and unique features is the “sharability”. You can share passwords with other NordPass users with utmost security and privacy. Only the intended party receives the passwords and no one else.
NordPass also features automated “Backup and sync“. This ensures that the passwords are always updated and available across all your devices, also comes in handy if your primary device is lost or corrupted. The data is encrypted before being uploaded to the servers making sure it remains yours and yours only.
It also supports OCR scanning, which can be used to automatically read/scan and store data from cards, pages and other similar physical printed materials. In case you’re using other password managers at the moment, it also supports “importing” passwords directly.
As for direct security, it supports not only 2-FA but also biometric authorization! So your fingerprints and voice can be used as for accessing NordPass.
Moreover, why just “store” passwords? It’s capable of churning out really (really) strong passwords in case you need them. They’re generated at random, and again completely inaccessible to NordPass.
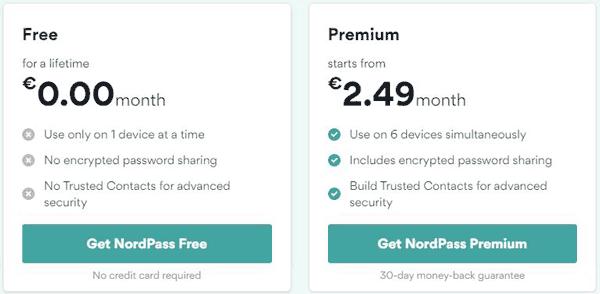
It’s available across all major devices and operating systems, including iOs, Android, Linux, MacOS, Opera etc. There’s a free plan with limited features (no password sharing / limited to 1 device) or a plan which costs EUR 2.49/month but offers all the features.
In a nutshell, every website you visit will get its credential-field populated automatically without you having to remember anything.
LastPass – Best Password Manager Tool
Website: https://lastpass.com/
LastPass is a Fremium tool, meaning it has both a free as well as a premium version, and in my personal experience, even the free version has more than enough features for most of us.
Now it’s a “secure vault” which saves all your passwords automatically for various sites whenever you login to those sites, or you can also add passwords manually.
Because it’s all on the cloud, you won’t ever forget a password no matter how many decades later you need it.
In addition to acting as a vault, it also acts as a “master key”, meaning you don’t need to remember hundreds of passwords for all your different sites. Rather, simply remember the one master password you set for LastPass, and this password will auto-fill any site’s password on their login pages.
Also, one LastPass can be used on any number of devices and accounts, so you can simply install LastPass on all your devices, and forget about remembering or typing passwords ever again on any of those devices.
There are some advanced features as well such as Saving WiFi passwords, creating Credit Card profiles for easy auto-fills, and even “emergency contacts”, obviously 2 Factor Authentication is available as well.
Are these passwords safe? Totally! LastPass uses AES 256 military grade encryption along with PBKDF2 SHA-256 PBKDF2 SHA-256 salt hash to encrypt whatever we save on the platform.
Also, whatever we save on LastPass is always a secret, even from LastPass. The encryption and decryption private keys are “device based” so even LastPass can’t access the saved passwords, along with the MasterPassword.
Bottomline, it’s literally one of the best privacy tools when it comes to passwords, and both its Premium as well as free versions are worth it.
1Password
Website: https://www.1Password.com
1Password is a premium tool, with a 30-day free trial period. It has three different plans, for single users, families, or large businesses.
Like most other password vaults, it too uses a master password which isn’t saved on the 1Password server or anywhere else, but only on your own device and this single password can be used to login to any number of sites (whose details are saved on 1Password).
It allows for unlimited passwords to be saved and easy auto-fills like LastPass, although it doesn’t seem to offer 2-Factor authentication yet.
It also lets you create separate vaults, and share only selected parts of it with upto 20 members (in the pro plan).
So in a nutshell, it’s another one of those privacy tools which save your passwords, and auto-fill them, keep them organized, let you share it with your team members or families and make life easier for you.
There’s a “Travel mode” as well, which temporarily removes any vaults which you feel need to be hidden so as to escape a hostile situation, or some kind of investigations, inspections such as on airports.
As for encryption, it uses the same 256-bit encryption as LastPass, although one of its advanced features is its 34 characters long secret key, which they claim eliminates the need of 2-FA and makes it virtually impossible to hack into your 1Password account.
DashLane
Website: https://www.dashlane.com/
Another password manager with similarities and differences to the two tools listed above.
Dashlane too is a premium tool, it has a free version which lets you save 50 passwords, or the Premium plan with unlimited storage (USD $3.33/mo).
The basics are the same, it saves and auto-fills passwords for websites. However there are some features which make it different.
Its Dark-web monitor is one such feature. The platform automatically scans the Dark web, as well as other sites for leaked info. Whenever there’s a breach, or it finds your information to be in one such leaked database you’re alerted letting you change the password instantly.
Secondly, it lets you share your accounts with family members, co-workers and friends without having to reveal your password!
The User-interface is an eye-candy as well. Information such as reused passwords, weak passwords and even compromised passwords can be monitored at a glance.
The premium plan even comes with an in-built VPN. The VPN lets us access IP addresses from 23 countries, and even has advanced features such as the Kill Switch. The Kill-switch is a feature which automatically turns off your entire internet connection in case the VPN connection drops, hence you’re never unprotected.
It even allows for unlimited devices to be connected to the VPN (it’s rare).
It has a “Secure-note” feature which lets users store sensitive information and notes apart from passwords safe and encrypted. Obviously there’s the password generator should you need it.
And finally, there’s an “Emergency” feature which lets you add “trusted contacts” who can access your data and accounts at a time upon their request.
I believe those privacy tools are enough to keep your passwords safe, aren’t they? Let’s move on to Search Engine Privacy for now, cause hey that’s important too.
Keeper
Website: https://keepersecurity.com
Keeper is a password manager that offers most if not all the features we seek in a password manager. It offers as many as 5 vaults. These are like “folders” where you can categorize different kinds of passwords.
Its 2-FA is exceedingly impressive. SMS, Fingerprints and TOTPs are supported. Even biometric (Face IDs) and USB security keys too can be used as 2-FA.
It does allow customizing the fields, so, not everything has to be an “username”. You can also save other data such as card number, license number and anything else.
Even previous versions of saved data can be recovered. Up to 5 emergency contacts can be added. The KeeperFill® both fills passwords and also generates strong password when required.
BreachWatch® add-on, when opted for, monitors dark web leaks and notifies you of potential damages.
It also can be used as an encrypted file storage system. Finally, the KeeperChat® add-on allows for encrypted chats and messages. This is best used for sharing passwords and other sensitive data.
Many different plans available, however, the “Personal” plan is the cheapest and starts at $2.91/month. There’s a 30-day free trial. Students also are eligible for a 50% discount.
Search Engine Privacy
This is an aspect of online privacy that’s ignored more often than we’d like to admit. Search Engines used by us track a large part of our online, primarily our search queries to begin with.
Then, the sites we visit, the time we spend on those sites, our locations, shopping preferences, and a lot more.
And it’s not just collection, they also share the information over either their own various products and networks, or with third-parties, primarily advertisers.
They even decide which results we “may” or may not like, generally it’s all well and good, but if you’re a privacy freak, you really wouldn’t want anyone intruding into your privacy, would you?
If you’re still not convinced it’s dangerous, here’s a live DATA LEAK from AOL that happened back in 2006, simply search for a keyword, and you’ll get “user numbers” of everyone else who searched for it, along with everything else that user searched for!
So, here are some of the best privacy search engine which do not track or monitor you and give you the privacy you’re entitled to.
DuckDuckGo
Website: https://duckduckgo.com
Duck Duck Go isn’t a new face to the game, and almost everyone has heard of it. It’s a Search Engine which prides itself on the fact that it doesn’t track any aspect of your online searches.
It doesn’t collect or monitor your search history, and because there’s no data collected, they also can’t sell anything to advertisers, and for the same reason DuckDuckGo also doesn’t show any ad on its Search Page, or anywhere else.
It without doubt is one of the best privacy tools and has been so for over a decade now, the reason being there are no ad-trackers, no “personalized suggestions” or anything else that’s “personal or private” to you.
Start Page
Website: https://www.startpage.com/
StartPage’s tagline itself says why it’s one of the best privacy tools because it gives us “Google” but without Google’s intrusive nature.
Obviously, Google is probably the best Search Engine out there, so what StartPage does is, when you enter a search query on StartPage, it submits it to Google, and then displays you the results, hence acting as an intermediary.
Because of this, Google never knows you searched for something, and hence could collect nothing.
It doesn’t store any IP addresses, search history, or anything else which can be used to identity or even personalize your preferences, so again it too is totally ad-free!
And just as with DuckDuckGo, as there’s no personalization, you get access to the exact same search results as everyone else, there’s no “filter bubble”, equality right?
Torch
Website: http://xmh57jrzrnw6insl.onion
Torch too is another search engine which doesn’t collect information about you, but it’s different from the above two in the sense that Torch also displays .onion links!
Yeah, you can search for Deep Web links on Torch and it won’t mind, and because it doesn’t track or monitor you, it’s completely safe as well.
Although, it does show ads but those ads aren’t “personalized”, rather just general, universal ads which are the same for everyone, and I personally understand the need to do so, it’s not easy to sustain a search engine specially with other giants like Google being around.
Another feature which differentiates it from the other two search engines we talked about is its “Media Grabber”, which is a downloader of sorts, letting you download any kind of media you come across.
In a nutshell, yeah it’s private, anonymous, and let’s you search for deep web links as well.
Anyway, Here’s a full list of Anonymous, decentralized search engines! Now let’s move on to the next section of this privacy tools guide.
Private.sh
Website: https://private.sh/
The search engine claims to protect your data “cryptographically”. It basically works as a “mediator” or a proxy.
All the searches are first encrypted on your device, and then proxied through the search engine. Basically, your IP address is hidden for each search.
Beware though, it doesn’t display millions of results as you may expect. The result index is fairly low and only spans to about a few hundred results at best.
It has two primary search modes, you can search for random results for your keyword, or “news”. You can even perform country-specific searches!
The platform is completely open-source as well further making sure it doesn’t have hidden agendas.
Advanced settings too are available, e.g. you can hide “objectionable” content, enable or disable thumbnails etc.
Instead of using the URL, you can also use its Chrome and FireFox addons. They make your searches anonymous even on those other browsers.
Hard Disk Security
So, by now we’ve talked a lot, but mostly about online privacy tools, it’s time we shift our attention to “offline security” as well.
Primarily Hard disk, file and folders security. Because that’s where all our private files and data resides isn’t it?
Now because most of your files or disks aren’t encrypted, there always is the risk of someone gaining physical access to your system and stealing them.
Or, if your system as a whole gets stolen or you send it for repair as well there’s no saying that the data won’t land in the wrong hands.
And if you’ve more advanced adversaries, the risk of them inflicting your computer with a Trojan Horse, or any other kind of virus and copying files remotely exists as well.
And that’s exactly why you need to encrypt your data, because when encrypted, even if someone does gain access to your system, or installs a virus, the data they’d get won’t be of any use to them (because it’s encrypted) and you’ll stay safe.
So that’s what the following privacy tools do for you, encrypt and secure your data, for free!
Website: https://nordlocker.com/
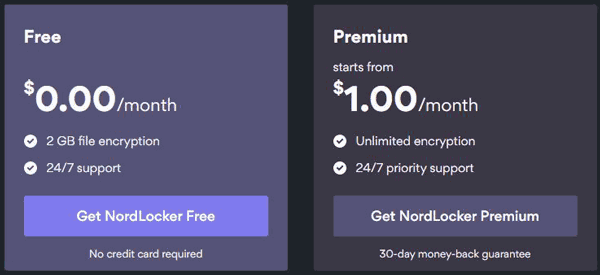
User-friendly, extremely secure, easy to use file encryptor is exactly what NordLocker is. Let’s start with the fact that it does offer a free version, so no you don’t have to pay a cent to use it.
Alike all the best privacy tools out there, it too offers zero-knowledge encryption. The company has no knowledge of what you store on the application.
My personal favorite feature with NordLocker is there are absolutely no complicated settings or encryption-keys on our part to take care of. We can simply “Drag & Drop” the files to the locker and they get encrypted, could it be any easier? Probably not.
Files often need to be shared, and that’s one of the most vulnerable times for them to be attacked. Well with NordLocker, you can share the file simply by entering an e-mail ID of the person you wish to share with. They’d receive an e-mail and would need to create a free NordLocker account and then simply access the files. Or, you can connect NordLocker to your Dropbox account, and simply share a link as easy as that.
This eliminates the need of a “password“, if there’s no password to begin with, no password can be “hacked“, smart! What if you lose your NordLocker password? No biggie, you can always restore your account using a “Recovery Key” which is presented when you first create your account.
It also can be used to secure your cloud storage by encryption files before uploading them to the web. The paid plan costs just USD $1.00/month and offers unlimited encryption.
VeraCrypt
Website: https://www.veracrypt.fr
We recently did a complete, detailed VeraCrypt review, VeraCrypt is probably one of the simplest and most secure disk and file encryption solutions out there.
The prime attraction is its “encryption on the fly” feature, meaning it doesn’t decrypt the files beforehand, but exactly in the moment when you need the file to read/ write or transfer.
The decryption is done on the RAM (when the file is being used), so the decrypted files never reside on your hard-disk, hence not showing any moment of weakness for hackers to steal it.
Other advanced features like a “Hidden Volume” inside a standard encrypted volume, and a completely hidden operating system as a whole are available as well.
The best part is it doesn’t “slow” your disks down, or encrypted files which is rare with most other encryption software out there.
It’s also open-source as well as free so it already has been vetted by anyone educated enough to do so hence making it one of the best privacy tools out there.
AxCrypt
Website: https://www.axcrypt.net
AxCrypt is a similar encryption software to Veracrypt, although it has both a free, as well as a paid version.
Some of its key features include its ability to let you interact and work with encrypted files and folders just as easily as with unencrypted files, a simple double-click is all they need to be opened.
Then there’s its mobile support, letting you access your encrypted files on mobiles phones as well.
It has an inbuilt system which deletes all temporary cache and plaintext files which in one or the other way can compromise your security.
With 128-bit encryption and Iterative key-wrapping, brute force or any other kind of attacks are kept at bay and guarantee you the security it claims to provide.
Here’s a more detailed list of best Encryption software you can refer to.
DiskCryptor
Website: https://diskcryptor.net/
Disk Cryptor is often considered one of the best Privacy Tools for Hard Disk Encryption. Infact, it’s considered to be one of the main rivals for Veracrypt!
It too is open-source, hence no centralized agency or company can have hidden backdoors. Moreover, it’s been here for over half a decade, which means it truly is secure and trustworthy, considering the lack of negative comments and experiences of other users.
It supports AES, TwoFish as well as Serpent encryption algorithms. It supports Hardware AES acceleration. Hence, the functional speed is pretty impressive, and there’s no major or visible difference between the Encrypted and Non-encrypted drives.
As for security, the key can be stored on a removable media and used while decrypting. Pre-boot authentication makes sure the system isn’t tricked into allowing access before a boot process is complete.
Can also be used to encrypt USB/CD disks apart from Hard-Disks. It also remembers the boot password, so if the same password is used for different files it needn’t be entered each time.
If you’re more of an advanced user, it can also be used with Command line instead of the standard graphical interface.
It’s a Windows-only program and doesn’t support any other OS for now. But then again it’s free, highly trusted and with proven security.
Email, Communication, File Sharing Security
So now we’re finally down to the last section of this privacy tools guide. Let me just discuss in brief why they play an extremely important role in privacy.
E-mails aren’t just “E-mails” anymore, they’ve turned into our online storage spaces, we send confidential files, confidential communications, unpatented projects, research work and what not over E-mails, don’t we?
And even for the most basic users, sharing their personal preferences and choices over E-mails is common.
In the least, E-mails can be used to determine our routines, when exactly an E-mail is opened, which links are clicked, which days or weeks we open most of our E-mails and all of that can be used to put together a timeline for our real lives, can’t it?
Even E-mail providers such as Gmail and Yahoo collect and share your information!
Another point that brings in the need for these use of privacy tools is that even if the general E-mail providers were safe and privacy respecting, the files we send over the E-mails or our communications can be intercepted by third parties and agencies which again is a massive privacy nightmare.
And even if you leave E-mails out, most other file-sharing services out there such as DropBox are products of centralized companies such as Google, Microsoft other companies which isn’t exactly privacy-conscious.
In fact, Edward Snowden clearly said “Get Rid of Dropbox” in one of his statements.
These companies not just hold ultimate hold over your data, but also won’t hesitate to cooperate with govt. or other third party agencies if and when the situation presents itself.
Bottomline, E-mail, file-transfer or communications privacy is of utmost importance and that’s what the next shipment of privacy tools hold for you.
CounterMail
Website: https://countermail.com/
CounterMail counters govt. surveillance. It uses OpenPGP 4096 bit encryption for encrypting the emails. In simpler words? No one, not even the CounterMail company or team has access to your emails. This isn’t just “policy”, it’s a technical impossibility for any third-party to gain unauthorized access to the emails.
The company also makes sure MITM (Man in the Middle) attacks are not possible by using RSA and other encryption on top of the standard SSL. Even the severs it uses are diskless.
In the future, it has plans of incorporating E2E instant messaging, delayed sending and self-destruct messaging features. Pretty clear why it’s a “privacy tool”, right?
IMAP servers, autoresponders, USB-passwords, custom domains and many other features are available. It’s an invite-only platform which makes it a lot more premium, spam-free and worth checking out, doesn’t it?
Skiff (E-mail client)
Website: https://skiff.com/
Skiff offers end to end encrypted emails for free. No other party gets access to these emails, not even the Skiff team.
The platform is completely open-source offering users like us the trust-factor and ability to verify its claims.
Some of its features include 2-FA, Metamask logins, a mnemonic code for account recovery, free aliases etc.
There’s even a productivity suite (yes, like Google Docs/Sheets etc.). that lets you invite, collaborate and work on projects along with your teammates, in real-time. This too is completely E2E encrypted and free.
Custom domains aren’t available as of writing this piece, however, they’re about to be integrated very soon.
ProtonMail (E-mail Client)
Website: https://www.protonmail.com
 ProtonMail is literally the best Anonymous E-mail service out there. With its servers located in Switzerland there isn’t much any govt. or third party agency can do to force it to share anything with them.
ProtonMail is literally the best Anonymous E-mail service out there. With its servers located in Switzerland there isn’t much any govt. or third party agency can do to force it to share anything with them.
In addition to that, the site doesn’t keep any IP or E-mail logs by itself anyway so nothing exists that can be shared in the first place.
ProtonMail is also open-source, so the code, and its no logs policy can be obviously verified.
Not to mention its peer to peer encryption which guarantees iron clad security to any and all E-mails send via Protonmail.
Tutanota (E-mails)
Website: https://tutanota.com/
Tutanota is another anonymous e-mail service that’s E2E encrypted alike Countermail or Protonmail. It encrypts everything including the sender’s ID, subject, body and attachments of an e-mail.
It’s 100% anonymous and doesn’t ask for any personal data, including name or phone numbers. It also doesn’t log IP addresses, rather, it strips the IPs from e-mail headers for added anonymity.
It’s also open-source, making it easy to verify its claims and security. As far as legal jurisdiction goes, it’s based out of Germany. It may not be as good as Sweden or Switzerland, however, it’s still one of the best countries as far as digital laws go.
Contacts, Calendar, White-labeling and 2-Factor authentication are some of the other available features. It also supports custom domains, aliases and custom filters depending on the plan you go for.
There sure is a free forever plan even though it offers lesser features. Do note that the encryption and security isn’t compromised on any of the plans. It has native clients for Desktops,Linux, macOS, iOS and Android making it portable and device-friendly as well.
ParanoidPI (E-mail Client)
Website: https://paranoid.email/
ParanoidPI is exactly what the name signifies, it’s paranoid! Especially when it comes to encryption and security.
First of all, it uses the “Paranoid Infrastructure” to route any and everything send via the platform which means even your unsecure IP address becomes “secure”.
Then, it uses the NAT cloak to encrypt and decrypt the mails, in simplest possible words it’s like a curtain which hides the process, keys and everything from prying eyes.
Its guaranteed encryption double-checks and makes sure the Emails are encrypted, they aren’t always. And when that happens, they encrypt the E-mail from their end.
So yeah, it’s as secure and anonymous as it gets!
OnionMail (File Sharing)
Website: https://onionmail.info/
OnionMail is a mail service which uses the Tor network, it provides 100% encryption to all E-mails by “not” using the traditional SMTP servers to send/receive mails and instead by routing the mails via the Tor network.
It also makes use of “Asymmetric keys” for dual protection, in addition to advanced level spam detection and filtration in the mailboxes.
What’s best is it also lets you select your server entry and exit nodes if you understand them.
Considering it uses the onion network, there’s no doubt of it being off-the-grid, and secure, especially from the govt. censorship and regulations.
Here’s a Detailed list of Anonymous and Private E-mail service providers!
Riochet (Instant Messaging)
Website: https://ricochet.im/
Riochet’s is a messaging service that “doesn’t trust anyone”. It has really implemented some hardcore features which make it one of the best privacy tools in existence.
For instance, it doesn’t use a “messaging server” so it can’t be hacked, rather it uses the Tor network.
There are no “usernames” or E-mails, rather random numbers that can be used to contact people.
All your messages, contact list and everything else lives on “your computer” and not on any server or on the cloud, so again, can’t be hacked remotely.
Then there’s end to end encryption so intercepting these mid-way is useless as the messages can’t be decoded by anyone else except the intended senders and receivers.
So yes, it’s one of the most secure instant messaging services available out there.
OnionShare (File-sharing)
Website: https://onionshare.org/
Onionshare is a file-sharing platform, available for Windows, Linux, MacOS, Ubuntu, Fedora and every other Linux distro.
The working infrastructure is what makes it unique, anonymous and highly trust worthy.
When a file is shared, it creates a temporary web server, on the Tor network, and gives you a random, long URL which is like a “download link” for your file.
Note that your computer acts as the “host” for the download link so you don’t have to trust any third-party service to host your files and the files are never actually “uploaded” online.
Also, you don’t have to share your name, email or anything else with the receiver hence keeping your identity a secret.
It even has a “stealth mode” which protects the URL against hidden Tor nodes which may try to gain access to the file. Not to mention that the files are encrypted end to end so yes they can’t be intercepted no matter what.
MailVelope (Mail Encryption)
Website: https://www.mailvelope.com/en/
MailVelope is what turns general, “not so secure” E-mail clients such as Gmail and Yahoomail into highly secure mail clients.
It’s simply a browser extension which uses the OpenPGP encryption algorithms to encrypt your emails directly from your mailbox to the mailbox of the other person.
Both you and your partner(s) need to use Mailvelope, and then the program lets you create private and public keys which can then be used to communicate securely.
The features remain the same as any other PGP encryption, such as verification of each other’s identity and secure encryption. As an additional feature, it also lets you sign your emails with a “digital signature” for verification of its authentication
It does not extremely feature rich but is clearly of the simplest and worth using online privacy tools.
CryptoCat (Instant Messaging)
Website: https://crypto.cat/
CryptoCat is again an instant messaging solution which lets you talk to your friends without compromising your security.
And it also uses a lot more hardcore encryption protocol than those commonly used messengers, such as using the double rachet based encryption which basically is a combination of forward secure rachet with zero round trip authenticated key exchange.
In simple words, it’s extremely secure. It also is open-source and open for audit by anyone.
As for privacy, it doesn’t need any of your personal information, and you can use a new username everytime you use it so no one knows who you actually are.
That been said, you can actually chat with your real-life friends where only you two know each other and no one else knows the two of you by using “Secret questions”.
In a nutshell, it’s fun, secure and private. And I can best explain it as a burner phone, those temporary cell phones you can just pickup at any store without any documentation, call, and ditch.
Tribler (BitTorrent client)
Website: https://www.tribler.org/
Tribler is a BitTorrent client which lets you search, stream and download content off the internet, without the need of any website.
Although what makes it one of the best privacy tools is the fact that it’s open-source, decentralized, and totally impregnable to govt. Censorship.
It’s like an anonymous “search engine” for files which lets you find and download files without sharing your personal information anywhere.
It also has some features of a social media, as it lets you add other users as your friends, and after a few downloads can “guess” your preferred types of content.
Also the users whom you add as friends can help you speed up your downloads by letting you use their upload capacities.
The downloads are encrypted, routed through the onion network and are seeded in a hidden mode. And it’s free as well as open-source!
So in a nutshell, if you download content off the Internet, something that you shouldn’t download normally, or is hard to find, Tribler is your solution.
You’re exhausted, I get it, so am I. Too much to take in? Bookmark us, read us couple hours later again maybe? Anyway let me sum it all up.
Wickr Pro
Website: https://wickr.com
Wickr raised USD $30Milllion worth of funds just after its USD $9Million Series A funding back in 2014. The founder Nico Sell is also the same person who organizes the Defcon conferences. So far, it can be trusted on its face-value.
Apart from that, its End-to-End encrypted communications ensures that no third-party apart from the sender and the receiver have access to the data, not even the company itself.
To reinstate the claimed trust, the company also offered a USD $100,000 bug bounty to security researchers who’re able to bring up potential vulnerabilities in the app.
Due to its nature, Wickr claims it’s unable to provide Law Enforcement with subscriber’s content (messages, files etc). even if it wants to.
Apart from the End-to-End encryption, another one of its prime features is the “Expiry-time” for messages. Users can set a time along with the message, once the timer expires or is reached the message self-destructs not just from the chats, but also from the Wickr servers.
You can use Wickr to Call, Video Call, or even Conference call a group of friends/team members and it’s all encrypted. Secure and encrypted Screen-sharing too is possible. It recently announced its “Screenshot detection” feature which notifies users if a screenshot is detected. Furthermore, there’s Overlay protection for Android devices which acts as its anti-tapjacking measure.
Rooms can be created, and moderators can be assigned to those rooms as well. Files of all types can be shared which too are encrypted. Other features include location sharing, and online status sharing. Available on Windows, iOS, Linux, MacOS, and Android.
Wire
Website: https://wire.com
Wire has multiple reasons why it won me over. For starters, it’s completely open-source and has been verified by multiple security teams across the globe. The reports have been transparently published for the world to read as well.
Then, it’s wrapped with European Security and Privacy laws. It has its H.Q in Switzerland, and uses servers from EU. Has a strict “No Selling of Private Data” Policy. Talking of private data, it doesn’t collect any. No name/phone numbers required to Sign up.
A random/anonymous E-mail can be used to Sign up. Usernames are completely random and can’t be linked with a person’s real-life identity either. It uses End to End encryption to encrypt the communications. Additionally, also provides for “forward and backward” Secrecy. This means it uses new keys for each message. So even if a set of keys are compromised, they can’t be used to decrypt past or future messages.
Also lets us verify partner’s (the receiver/sender) fingerprints to ensure it really is them and that the devices haven’t been tampered with. There’s a warning message, and a change in shield-icons which indicates the other partner of any device-changes. Is GDPR-compliant.
For us as users, it’s a communication, file-sharing and collaboration app. The primary features in those regards include encrypted messaging, group chats, voice/video-calls/messages, video-messages etc. Sharing Files, group-conversations etc too available. Doesn’t show any ads.
Available cross-platform on Windows, Android, iOS, Mac, Linux and even as browser-extensions!
How to choose the best privacy tools
Apart from the ones mentioned above, there are a number of other privacy tools you can get on your own.
While doing that, just make sure you try to tick as many of the following boxes as possible:
- Open source: open source software has its code open for public audit. This ensures the software doesn’t have any backdoors installed.
- Paid apps: Most open-source apps will be free. However, it’s a good idea to go with apps which ask you upfront for their money. Point is, if an app isn’t open-source, and if it’s still free, your information is probably how they’re making money.
- Jurisdiction: It’s important you pay attention to “where” a software is based out of. E.g. NordVPN, even though isn’t open-source or free is based out of Panama. It’s best to avoid tools based out of U.S or any country which is a member of the Five-Eye alliance.
- End-to-End encryption: This doesn’t apply to everything, however, when it comes to apps for communication, instant messages or e-mails, always look for tools which are end-to-end encrypted.
Payment Security- Cryptocurrencies
A major part of online privacy is breached by “payment records”, right? Everyone buys something online. While doing so, you probably use credit /debit cards, internet banking or online wallets. All of which are extremely transparent.
What if you could make payments, buy and sell things without revealing your identity? That’s where Cryptocurrencies come in.
Cryptocurrencies, primarily Bitcoin, is a digital mode of payment. These can be purchased anonymously, and then used to make payments. These payments can’t be traced back to you personally. You can read more about What is Bitcoin and how it works here.
As a tool, “Electrum” is a free Bitcoin wallet, open-source and pretty secure. You can download it to store your Bitcoins, and then make payments online.
What can you purchase with Bitcoins? Almost anything (even Space tickets, for real). We compiled a list of 100+ websites accepting Bitcoin payments.
In a nutshell, ditch normal (fiat) payments and switch to Cryptocurrencies. Fun fact: If you bought even $10.00 worth of Bitcoin in 2010, you’d have over USD 10 million today. So yes, they’re a great investment as well.
Final Words on the Privacy Tools
Hence ends this massive guide on Privacy tools. Trust me, I’ve tried to cover as many topics and tools as humanly possible without repeating myself or boring you to death.
And if you glance over this piece, I’ll say you’ll find I’ve included just about every one of those best anonymity tools that exist in here.
I’ve covered online, offline, communications, file-sharing and every other kind of security that most of you should be aware of.
And let me just assure you, there aren’t many tools which I’ve included here but don’t use myself, so yes most of these are vetted personally by me so feel free to use them.
Anyway I’m burned out, so I’ll stop typing, just let me know what you think of this piece and the privacy tools shared here our Facebook page, along with your questions, tips and feedback.